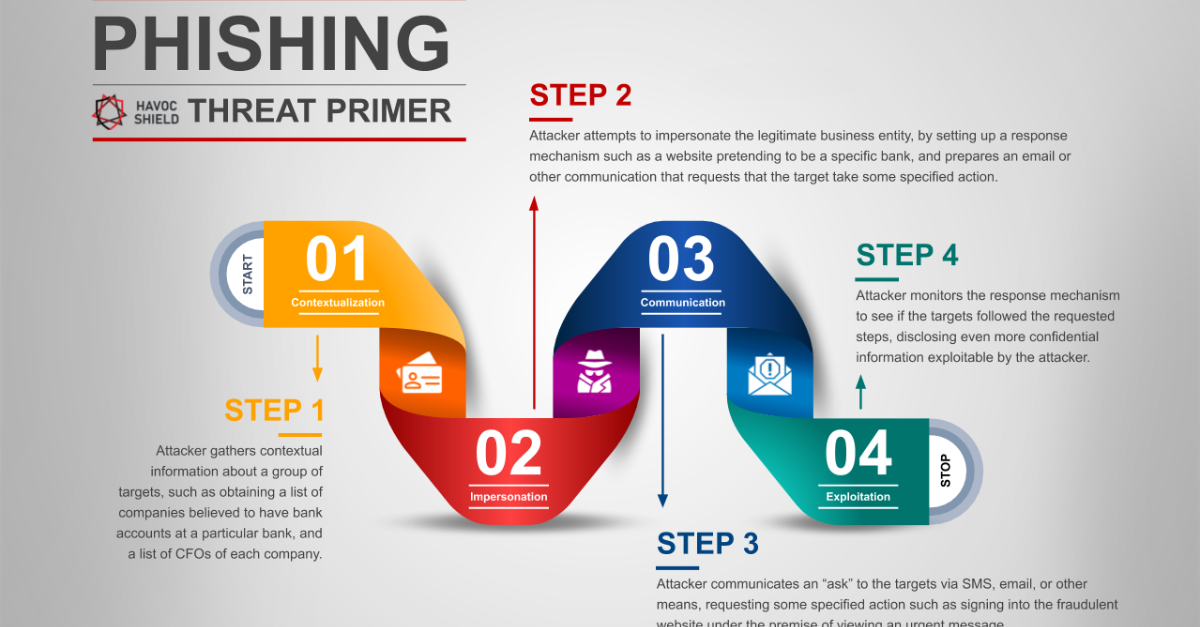
How to spot phishing emails in 2025
Spotting a phishing email in 2025 is more important than ever. Despite growing security awareness, knowing how to spot phishing emails in 2025 can help you protect your personal information...
Phishing remains one of the most dangerous and widespread cybersecurity threats in 2025. Despite increased awareness and advanced security systems, cybercriminals are constantly refining their tactics to deceive users.
To successfully navigate online interactions, understanding how to spot phishing emails in 2025 is essential for everyone.
Continually updating your knowledge on how to spot phishing emails in 2025 can make a significant difference in your online safety.
Being aware of how to spot phishing emails in 2025 involves recognizing common signs and knowing what actions to take.
As the year progresses, the tactics used by cybercriminals evolve; therefore, learning how to spot phishing emails in 2025 is crucial.
According to the 2024 State of the Phish report by Proofpoint, 86% of organizations were targeted by phishing campaigns last year, and over 70% of them suffered a successful breach due to human error. Meanwhile, the UK government’s Cyber Security Breaches Survey 2025 reported that phishing now makes up 93% of all cybercrime incidents in the country.
Take time to study how to spot phishing emails in 2025 to make informed decisions about the emails you receive.
The first step in understanding how to spot phishing emails in 2025 is recognizing the characteristics of suspicious communications.
By learning how to spot phishing emails in 2025, you can safeguard your online presence from potential threats.
Why is phishing still so effective? Because it bypasses systems and targets people—often exploiting urgency, fear, or curiosity to trick victims into clicking dangerous links, opening infected files, or sharing personal information.
In this article, you’ll learn how to spot modern phishing emails, recognize red flags, and avoid falling victim—with updated tactics and real-world examples from 2025.
✅ Quick Phishing Detection Checklist
If you answer yes to any of the following questions, treat the email with caution:
📧 Sender & Domain
- Does the sender use a public email address (like @gmail.com) but claim to be a company?
- Is there a suspicious domain or a slight misspelling in the address (e.g. amaz0n.com)?
- Does the sender’s email differ from how that company usually contacts you?
📝 Content & Style
- Are there grammar or spelling mistakes?
- Does the message push for urgent action or use fear-based language?
- Is the tone inconsistent with past emails from this sender?
🔗 Links & Attachments
- Do the link URLs mismatch the displayed text?
- Are there unexpected attachments?
- Are the call-to-action buttons vague (e.g. “Click here”, “Confirm now”)?
🔒 Security Pressure
- Are you asked for passwords, personal information, or sensitive credentials?
- Does the message tell you to bypass normal protocols?
- Are there threats of negative consequences if you don’t act immediately?
If anything feels suspicious, pause and verify using an independent, trusted communication method.
“In Pakistan, phishing attacks continue to rise, making it essential for individuals and businesses alike to know how to spot phishing emails in 2025 to protect their sensitive information.”
🚩 1. Suspicious or Generic Email Domains
Legitimate organizations rarely use public email domains for business communication. If an email claiming to be from a major company arrives from an address like support-team123@gmail.com, it’s a red flag.
Reputable companies use professional domains (e.g., @google.com, @chase.com). Scammers often count on people not checking the actual address—especially since 85% of people now open emails on mobile, where only the sender’s name may be shown.
✅ Tip: Tap or hover over the sender name to reveal the real email address.
🚩 2. Slightly Modified Domains
As phishing attacks become more sophisticated, understanding how to spot phishing emails in 2025 is essential for everyone.
Cybercriminals frequently register domains that closely mimic real ones, tricking users into clicking malicious links or sharing sensitive info.
Learning how to spot phishing emails in 2025 can empower you to act quickly and effectively against potential threats.
Keep in mind that knowing how to spot phishing emails in 2025 can help both individuals and organizations stay secure.
For instance, in early 2025, scammers launched a phishing campaign using micros0ft-teams.net (with a zero instead of an “o”) to trick users into entering credentials on a fake Microsoft Teams portal.
Just one unnoticed character can be enough to compromise your account.
✅ Tip: Slow down and double-check the spelling of all URLs—even a minor typo could be a trap.
🚩 3. Grammar Mistakes and Awkward Language
While phishing emails are increasingly polished—sometimes even generated by AI—many still contain awkward phrasing or minor grammar issues.
If the language seems off, ask yourself:
- Does it sound like a native speaker wrote it?
- Are words used strangely or in the wrong context?
- Is this a formal message that should’ve been professionally written?
- Does it match the tone of previous communications from this person or organization?
✅ Tip: A single typo isn’t always a red flag, but combined with other clues, it can confirm suspicion.
🚩 4. Dangerous Links or Attachments
All phishing emails share one thing in common: a payload. Whether it’s a link to a fake website or a malicious attachment, the goal is to steal data or install malware.
🧷 Malicious Links
In January 2025, fake emails impersonating Chase Bank used chase-secure-login.com, luring users into entering credentials on a spoofed site.
✅ Tip: Always hover over links before clicking—check if the actual URL matches what’s displayed.
🗂️ Suspicious Attachments
Phishing emails often disguise malware as invoices, tax files, or other official documents. A March 2025 IRS-themed scam used ZIP attachments that installed malware when opened.
✅ Tip: Never open unexpected files. And never enable macros unless you’re 100% sure the source is trustworthy.
🚩 5. Emotional Manipulation: Fear and Urgency
Scammers exploit your emotions to rush decisions. The more pressure they create, the less time you have to think critically.
Some recent examples include:
- “Your parcel is being returned – reschedule delivery within 30 minutes.”
- “Google Ads account suspended – confirm billing now.”
- “Policy violation – click here to respond before escalation.”
These messages tap into your instincts—fear of loss, desire to fix an issue, or pressure to respond to a boss.
✅ Tip: Take a moment to breathe. Even if the message looks urgent, verify it through a second channel (such as logging in directly on the service’s official site or speaking to your manager).
🔒 Final Advice: Stay Skeptical, Stay Safe
Phishing attacks succeed by preying on trust and haste. The best defense is a calm, critical mindset and awareness of modern scam tactics.
What you should always do:
- Double-check sender addresses and URLs.
- Think before you click or download.
- Verify suspicious emails through separate channels.
- Report phishing attempts to your IT team or email provider.
Cybercriminals are getting smarter, but so are we. Share this guide with your team or community and help build a culture of awareness.
“How to spot phishing emails in 2025“
Make it a habit to remind yourself how to spot phishing emails in 2025 whenever you check your inbox.
Adopting a proactive approach to email safety this year can greatly enhance your personal security.
By regularly updating your strategies, you’ll stay ahead of cybercriminals who evolve their phishing tactics every day.
Together, we can create a safer digital environment by staying informed and sharing tips on how to identify phishing attempts.
Ultimately, mastering how to spot phishing emails in 2025 is key to protecting not only yourself but those around you.
As you apply these techniques, remember: email awareness is a critical skill in 2025 and beyond.
Stay informed, stay cautious, and stay protected.