“Officer, I was only taking a look at this company’s network security posture. I wasn’t stealing or breaking stuff. So how can I be guilty of anything?”
This might sound like a reasonable defense. Trouble is, the law doesn’t always see it that way.
Port scanning involves checking out a network for “open doors.” It’s used by threat actors to identify network vulnerabilities capable of being exploited. This technique also forms a valuable part of the ethical hacking toolkit.
But is port scanning legal? The short answer is, “it’s complicated.”
Most regulators across the globe take a dim view of accessing third-party systems without specific authorization. This is the case even if your activities are relatively non-invasive and your intentions are non-malicious.
So whether you’re a seasoned ethical hacker or a cyber security newbie just experimenting with port scanning, it’s important to know the law.
If you want to understand better this conundrum, keep on reading.
Ports and Port Scanning Explained
What’s the purpose and significance of ports? How does port scanning work?
Let’s take a closer look.
What Are Ports?
Multiple and varied categories of data flow between devices over a network. Ports are the docking points for the flow of this information.
They’re software-based and are incorporated into each device’s operating system, and they’re standardized across all devices and numbered according to a universal system governed by the IANA (Internet Assigned Numbers Authority).
There are 65,536 ports in total.
Those numbered 0-1023 are well-known ports, used for common internet-related activities.
1024 through 49151 are registered ports used by software vendors in relation to specific services.
49152 through 65535 are dynamic ports, capable of being used by anyone to aid network communication.
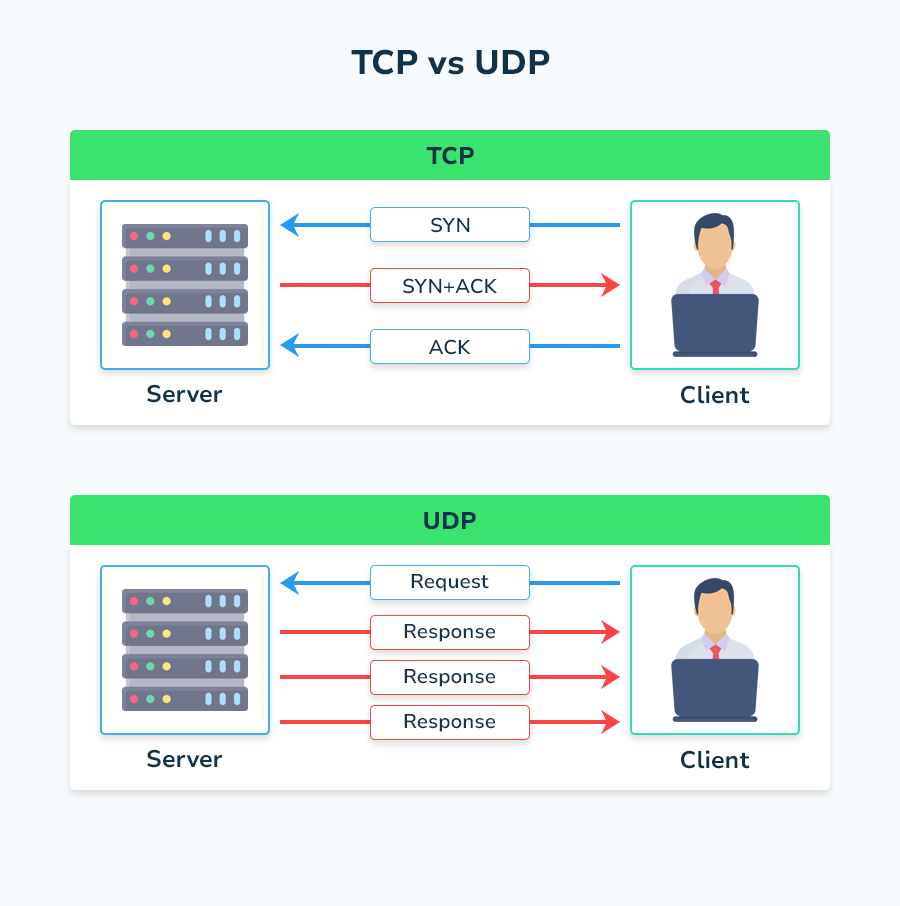
Each port is managed by one of two protocols: the Transmission Control Protocol (TCP), which defines how to establish and maintain a network conversation between applications, and the User Datagram Protocol (UDP), which is used mostly to establish low-latency connections.
TCP and UDP
With TCP, the host sending data sends a confirmation request after each data packet to ensure it was received before sending another. This is good for sending data where missing pieces will make the entirety inaccessible or damaged (such as HTML pages, images, documents, and programs).
With UDP, the host simply sends the data without confirming receipt. This is useful where speed is a priority and the occasional dropped piece of information isn’t critical. UDP transmission is used for steaming music and video, VoIP calls, and online gaming.
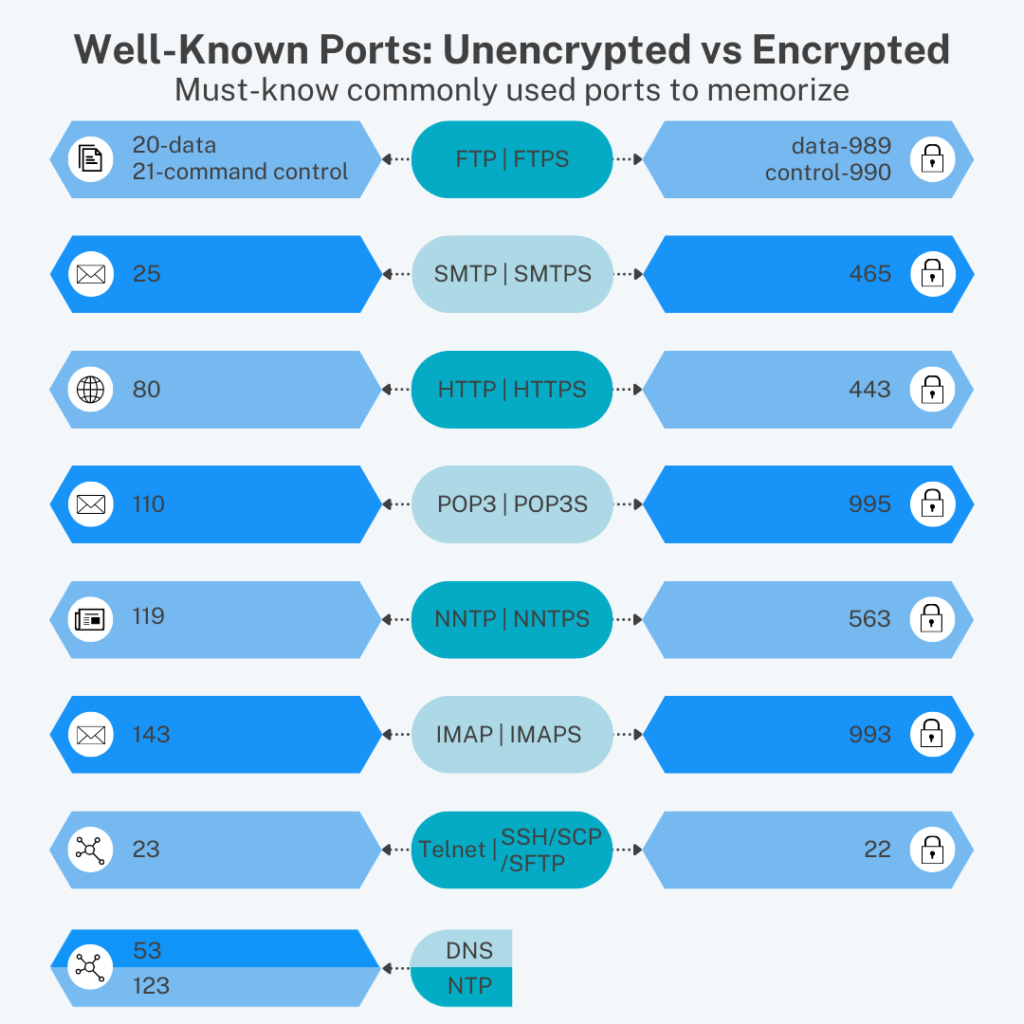
Some of the most important ports you’ll come across include the following:
- Ports 20 and 21: File Transfer Protocol, for transferring files between a client and a server.
- Port 22: Secure Shell (SSH), one of the main tunneling protocols for secure network connections.
- Port 25: Simple Mail Transfer Protocol (SMTP), used for email.
- Port 53: Domain Name System (DNS), makes the internet workable by matching human-readable domain names to machine-readable IP addresses.
- Port 80: Hypertext Transfer Protocol (HTTP), the default port for sending and receiving unencrypted web pages.
- Port 443: HTTP Secure (HTTPS): All HTTPS web traffic goes to HTTPS, the encrypted version of HTTP.
- Port 500: Internet Security Association and Key Management Protocol (ISAKMP), often used to set up VPNs.
What Is Port Scanning?
Port scanning is a method for detecting which ports are open—i.e., capable of sending and/or receiving data on a network.
A port scan starts with a process of discovery, such as picking up all the active hosts on a network and mapping these hosts to their IP addresses. Next comes the actual port scan.
A few of the most common broad techniques for scanning are as follows:
- Sweep: Where you scan the same port across multiple machines in order to elicit an echo response. If you get a response, it can indicate the absence of firewalls and other perimeter defenses on the target network.
- Vanilla: An attempt to connect to all 65,535 ports to see what comes back.
- Strobe: A highly-targeted scan, looking for specific ports and services.
- Fragmented packets: By sending fragmented packets to test the status of specific ports, you may be able to bypass a firewall’s packet filters.
- Stealth: The scanner is able to—or attempts to—block the target computer from recognizing that a scan is in process.
As a penetration tester, an infosec pro, or a network administrator, you’re almost certainly going to be using a dedicated tool for your port scanning. Nmap, an open source app, is the most popular. Others include Unicornscan and Zenmap.
Why Would Someone Port Scan?
You see this a lot with cyber security: the same tool or technique being used by security professionals as well as threat actors. Here’s how port scanning is put to work for both good and bad.
Port Scanning and Cyber Attackers
As an offensive tool, port scanning helps threat actors (black hat hackers) carry out reconnaissance and lay the groundwork for delivering a malicious payload.
Stealthy techniques are often used to evade a system’s perimeter defenses.
For instance, a slow scan—such as configuring your port scanning tool to operate at a slow rate—helps the scanning packets blend in with regular network traffic, making it harder for intrusion detection tools to identify anything irregular.
Armed with information gathered, attackers can hone their attack—e.g., brute force attacks targeted at specific ports, exploiting known vulnerabilities, or deploying malware.
Port Scanning and Authorized Cyber Security Use
Effective cyber security is all about staying one step ahead of potential threat actors. As such, port scanning is key to identifying and fixing vulnerabilities before they’re exploited. This is where security auditors and penetration testers (white hat hackers) enter the picture.
Why is this port open? Is it serving a purpose for our organization? What services—if any—depend on this?
Regular scanning helps you map out your network, understand its topology, and establish effective security controls. A big part of this includes configuring firewalls to ensure that only necessary ports are accessible and that unauthorized traffic is blocked.
“After-the-event” port scanning can also help you with incident response—e.g., detecting rogue applications that may already have been installed and are quietly active, or reviewing historical scan results to help trace the origin of a breach.
Port Scanning and Unauthorized Pentesting
Gray hat hackers often use port scanning in a similar way to authorized cyber security professionals. The main difference is that they’re acting without the permission or knowledge of the system owner.
For instance, let’s say you’ve probed a system and identified various entry points that ought to be closed. You then use this information as the basis for a vulnerability assessment which you can present to the system owner.
Alternatively, you could follow up the initial port scan with further pentesting steps. For instance, you could discover what specific directories or applications are exposed for a more detailed vulnerability assessment, complete with recommended mitigation steps.
Again, you’ve not sought out or received consent to do this from the system owner, though you have no ill intent. Is this type of port scanning illegal? Once you step into the arena of unauthorized scanning, that’s when it gets complicated.
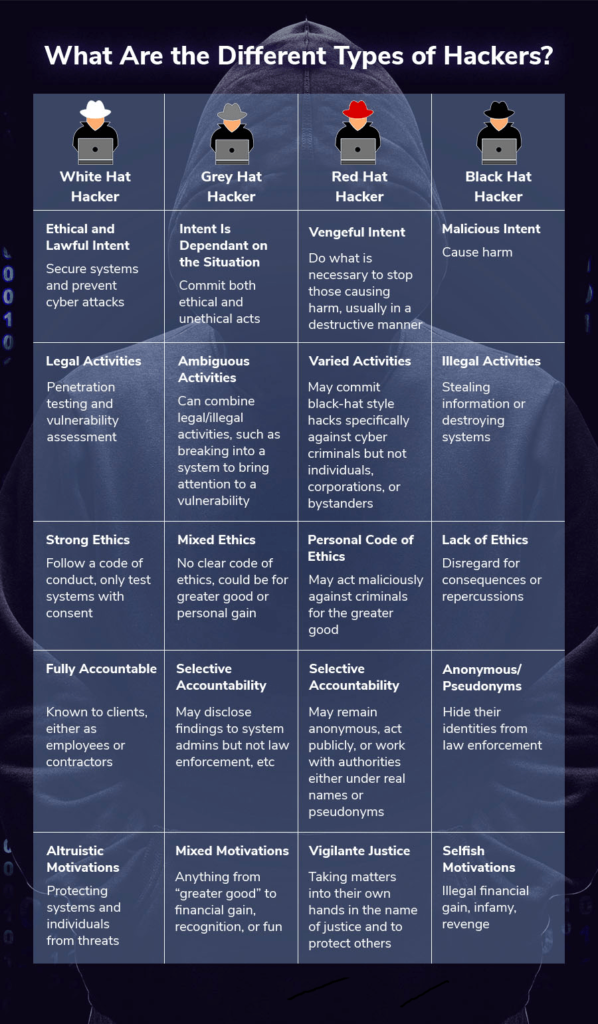
What Are Legal Issues with Port Scanning?
Is port scanning illegal? To help you understand this, we’ll take a look at some general principles, as well as examples of specific rules in place across key jurisdictions.
The Emphasis on “Unauthorized Use and Access”
Law-makers don’t want to keep going back to the drawing board to revise existing legislation if they can help it.
This is especially relevant when it comes to technology. Things move fast, and if they tried to compile long lists of specific activities they want to prohibit, they’d be forever adding to the rule books.
So, no matter where you’re based, you’ll likely find that the laws surrounding computer fraud and misuse are expressed in deliberately general terms. The issue of authorization is crucial, and there’s usually a provision prohibiting “unauthorized use” or “unauthorized access” to computers and anything stored on them.
Such provisions often come with strict liability. That is, it doesn’t matter why or precisely how you accessed a computer—or even necessarily what its consequences were. The fact you did it without authorization is sufficient for you to have broken the law.
As with any kind of “uninvited” freelance pentesting work, you should look carefully at the rules in place in your jurisdiction. Be aware that port scans will technically fall into the category of unauthorized use when done without specific permission.
Prosecutorial Discretion
According to the letter of the law, port scanning may be illegal in your country.
But of course, if prosecutors decided to pursue every single technical infringement, most legal systems would collapse pretty quickly. So there’s almost always an element of prosecutorial discretion—accompanied, one would hope, with a healthy dose of common sense.
For instance, let’s say you run an unauthorized scan on a large business. They don’t like it and alert the authorities.
On questioning, you’re able to show that you had no malicious intent, no data was accessed, and no damage was done. You would hope that common sense would prevail and no further action would be taken.
But the problem with discretion is that it’s not you who gets to decide when it’s exercised.
Let’s say the authorities don’t like your attitude—or your prior record—or the business in question really doesn’t like being “hacked”—(as they see it—and holds plenty of sway: you may find yourself on shakier ground.
Or maybe it wasn’t a business you targeted but a government office, energy provider, or healthcare facility. Again, these are situations where discretion is a lot less likely to be exercised in your favor.
Unintended Impacts
“It’s only a scan. What harm can it do?”
The physicists among you may be aware of a theory known as the observer effect: the idea that merely by observing or measuring something, you unavoidably alter or interfere with it.
Something kind of similar applies to cyber security.
Any scan or other activity you run on a target system will have some impact on it in terms of things like CPU, memory capacity, or network traffic speed. This may be negligible (a quick strobe scan), or it could be very real (e.g., multiple enterprise-wide sweeps conducted during peak trading hours).
Also, if you’re being investigated in connection to unauthorized port scanning, think about the actions that led up to this point. It was discovered, somehow.
Most likely, an internal security staffer or external MSP administrator got an alert. They had to stop what they were doing, investigate, escalate, and report. This is all time and money.
Be very wary of trying to defend unauthorized port scanning on the basis that no damage was done. There may be technical impacts and commercial consequences that you’ve failed to appreciate.
Is Port Scanning Legal in the United States?
Main governing law: The Computer Fraud and Abuse Act (1986)
- The Act makes it a criminal offense to gain “unauthorized access” to a computer.
- In June 2021, the Supreme Court decision in Van Buren provided direction on port scanning. The court held that mere violation of access restrictions is not necessarily an offense. Rather, the prohibition is limited to someone who “accesses a computer without authorization but then goes on to obtain information in particular areas of the computer—such as files, folders, or databases that are off limits to him.”
Is Port Scanning Legal in the United Kingdom?
Main governing law: The Computer Misuse Act 1990
- Section 1 of the Act stipulates that a person is guilty of an offense if they cause a computer to perform any function with intent to secure access to any program or data held in any computer, where that access is unauthorized.
- At present, there is an absence of clarity on the legal status of port scanning in the UK where the scanning is carried out without express authorization.
How Can I Scan Ports Legally and Ethically?
To stay on the right side of the law, it’s worth considering the following:
- Check the specific laws and any accompanying guidance that exists in your country.
- Remember that the safest option is to always get written authorization from your target before you scan.
- Several years ago, US Department of Justice Special Counsel Leonard Bailey gave advice at the Black Hat conference on how to stay out of trouble. The advice probably holds up well in lots of jurisdictions: “If you’re pinging a network, that’s not actionable. If you’re port-scanning, again, not a problem unless you’re doing it at a denial-of-service level. Beyond that, you may get questions.”
- Stay away from port scanning critical infrastructure and government sites.
- If you’ve been hired to port scan and pen test, stay strictly within the limits of the agreement.
- Your company might work with external partners whose systems are very closely linked to yours. Shipping and other supply chain actors are prime examples. To keep your own network safe, it’s a very good idea to port test these third-party devices. However, best practice dictates that you get written authorization from them to do this.
Conclusion
Research in the form of unauthorized port scanning is not without risk.
Remember that the chances of prosecution might be slim, but it still remains a possibility. Check the rules where you live, and be careful.
If you want to dive deep into cyber security, consider a AEC Membership. We offer thousands of courses and labs covering all aspects of cyber security.
Your membership comes with unlimited mentorship, certification and career roadmaps, study and mastermind groups, and an active community of students and professionals to motivate you on your journey.