What is Threat Modeling?
Threat modeling is a structured approach used to identify, assess, and mitigate security risks in a system, application, or network. By analyzing potential threats and vulnerabilities, threat modeling enables organizations to design more secure systems proactively or implement improvements to systems already in place. The threat modeling process can vary depending on the organization but normally involves defining security objectives, mapping out system architecture, identifying possible threats, contextualizing those threats, and automatically implementing mitigations based on the assessed risk.
Typically, threat models are created by cybersecurity professionals, security architects, and IT teams within an organization. These experts work together to incorporate insights from business, development, and operations teams, ensuring that the model aligns with the organization’s aggregate goals and risk tolerance.
Why Create Threat Models?
Threat modeling enables organizations to proactively identify and mitigate potential security risks before they can be exploited. By analyzing and understanding how a system could be attacked, organizations can prioritize what are often limited resources to address the highest-risk vulnerabilities, reduce the likelihood of breaches, and safeguard sensitive data. Creating threat models helps teams systematically evaluate their systems from an attacker’s perspective, providing a more accurate understanding of vulnerabilities and how they may be targeted.
Beyond just strengthening security, threat modeling enables compliance with regulatory standards and enhances overall resilience by ensuring systems are designed with security in mind from the outset. It also provides an actionable framework to foster collaboration across development, operations, and security teams, promoting a security-conscious culture that integrates protection measures across both operational workflows and the system’s lifecycle. This proactive approach can save significant costs related to potential incidents and bolsters hard-won customer trust by demonstrating a commitment to security.
Steps Involved in Creating a Threat Model
Step 1: Define Security Objectives
Defining security objectives at model’s inception provides alignment and clarity on the organization’s risk tolerance, key assets, and the critical processes that need protection (which is, frankly, all of them). Without a clear and cohesive understanding of what needs to be protected and why, the threat modeling process can lack focus, potentially overlooking significant vulnerabilities and wasting expensive staff hours. Security objectives should align threat modeling with the organization’s broader security and business goals. This first critical step ensures that resources are directed toward protecting what matters most to the organization, such as customer data, intellectual property, or operational continuity.
Step 2: Diagram the System
In this step, the team creates a detailed system architecture diagram to illustrate components, connections, data flows, and users. This visual map enables security teams to identify areas where data is most exposed and where potential attackers are most likely to try and gain unauthorized access. Diagramming reveals weak points and vulnerabilities within the system architecture and is crucial for understanding how an attacker might navigate the system and exploit security gaps. This step also helps potential gaps or weaknesses in the organization’s attack surfaces — points of entry that adversaries will very likely target.
Step 3: Identify Threats
Identifying threats involves considering potential adversaries and their methods (TTPs – tactics, techniques, and procedures) for attacking the system. This includes exploring common attack patterns, such as SQL injection or phishing, and imagining how attackers could use these techniques against the system components in the previous step. This step leverages contextualized real-world threat intelligence to anticipate possible attacks, which aids in designing defensive measures tailored to identified threats. By understanding potential threats, organizations can develop actionable insights and more effective security controls.
Step 4: Determine and Prioritize Risks
After identifying threats, the team assesses and prioritizes the associated risk, which will help focus remediation efforts on the most critical issues. This risk assessment considers both the likelihood of an attack and its potential impact on the organization. Risk prioritization helps the security team allocate resources efficiently. By focusing on high-risk vulnerabilities first, organizations can mitigate the most dangerous threats before they are exploited and/or achieve lateral movement. This is particularly important for optimizing budget and resource allocation.
Step 5: Develop Mitigations
In this step, security teams create strategies to counter the identified threats and risks, including new security controls, updates to existing protocols, or changes in system architecture. The goal is to mitigate identified vulnerabilities before they can be exploited, reducing the risk of data breaches and system compromise. By identifying effective security controls, this step strengthens the system’s resilience and aligns with compliance and regulatory requirements.
Step 6: Validate and Review
After implementing mitigations, it’s essential to validate and review the threat model to ensure that the security measures are effective and that no new vulnerabilities have emerged. This step involves verifying that the system behaves as expected and that new features and changes have not introduced additional risks. This validation step ensures the effectiveness of the threat model, offering assurance that the system is secure against the identified threats. It also sets up a framework for continuous improvement as new threats emerge and systems evolve.
Threat Modeling Best Practices
To optimize threat modeling and maximize security, consider the following best practices:
1. Integrate Threat Intelligence from the Start
Integrating a threat intelligence platform like Anomali ThreatStream adds real-world data into your threat modeling process, enriching the identification and prioritization steps. Threat intelligence also helps organizations understand specific threats that may target their industry, making threat modeling more tailored and effective.
2. Automate, Where Possible
Automation can help streamline the repetitive tasks in threat modeling, such as updating asset inventories or identifying common vulnerabilities. Integrating ThreatStream with SIEM, SOAR, or vulnerability management tools enables automatic flagging of vulnerabilities relevant to your specific threat model.
3. Engage a Cross-Functional Team
Threat modeling is most effective when it incorporates input from multiple departments, including IT, security, compliance, and business units. Collaboration ensures a holistic view of risks and prioritizes business-critical assets appropriately.
4. Document and Update Regularly
The bad guys never take their foot off the gas. This means your threat models cannot be static; they need to evolve as the organization’s systems, threats, and risk profiles change. Regular and frequent updates, along with detailed documentation, help maintain a current view of security posture.
5. Emphasize Training and Awareness
Equip security teams with the skills and knowledge required for effective threat modeling. Regular training on new tools, frameworks, and threat intelligence platforms will ensure they are prepared to address evolving threats.
Threat Models in Anomali ThreatStream
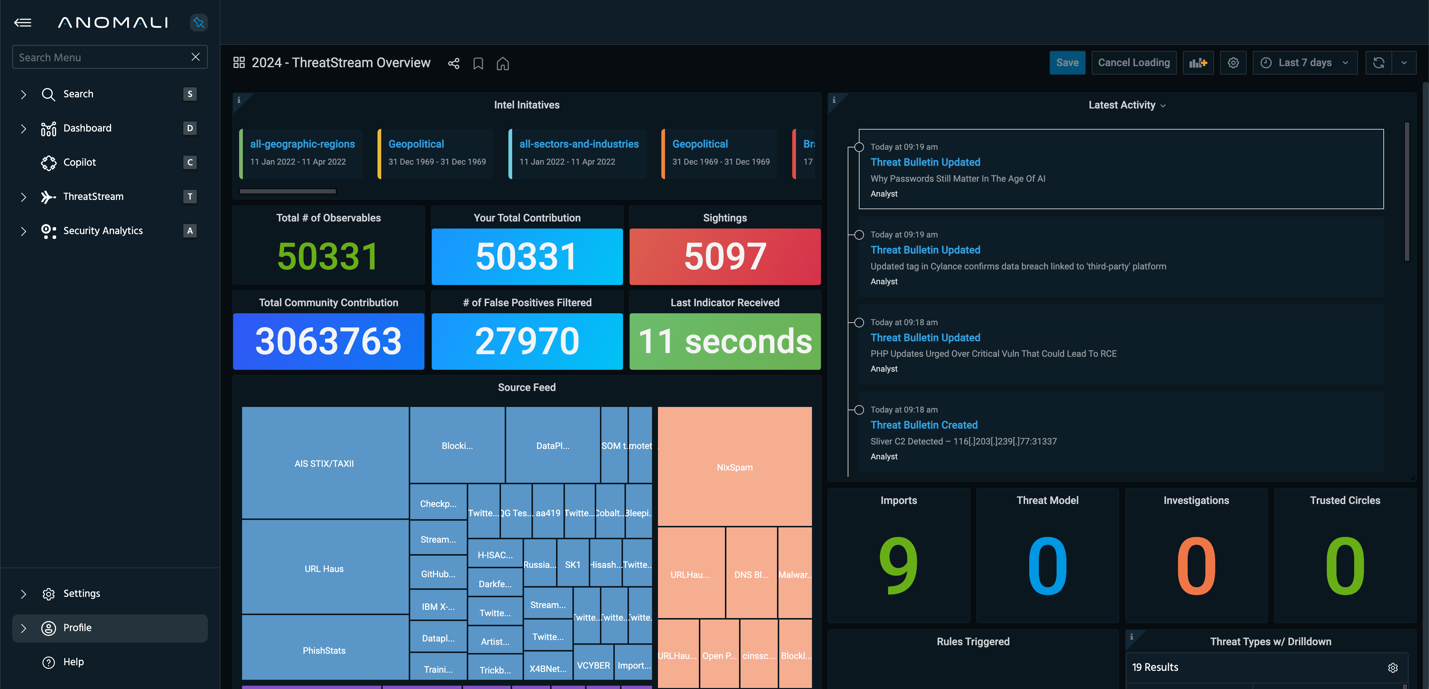
Fig 1. ThreatStream provides an immediate overview of critical security data points, including sources and context of threat data, real-time status on updates, and correlation to intelligence initiatives.
Anomali ThreatStream offers several powerful features that enhance threat modeling, making it a valuable tool for organizations aiming to improve their security posture. Some of the threat modeling features that have kept ThreatStream as the market leader for years include:
1. Comprehensive Threat Intelligence Integration
ThreatStream aggregates threat intelligence from multiple sources (OSINT, commercial, and premium), providing real-time insights on emerging threats, attacker tactics, and indicators of compromise (IOCs). This capability helps organizations keep their threat models up to date with the latest intelligence, ensuring that their defenses align with current attack trends.
2. Automated Threat Correlation
With automated correlation, ThreatStream maps detected threats to known vulnerabilities and attack vectors, streamlining the process of identifying relevant threats. This saves time in threat modeling, as security teams can quickly see which threats are most likely to impact their systems.
3. Advanced Threat Scoring and Prioritization
ThreatStream uses machine learning to analyze and score threats based on factors such as prevalence, potential impact, and relevance to the organization. This sophisticated capability helps security teams prioritize threats based on actual risk, enabling more targeted and efficient mitigations within the threat model.
4. Contextual Threat Enrichment
ThreatStream enriches IOCs with detailed context about threat actors, geolocation, targeted industries, and attack vectors. This contextual information allows security teams to develop threat models that account for specific adversary behaviors, providing a more realistic simulation of potential attacks.
5. Integration with Security Stack
ThreatStream integrates seamlessly with the Anomali Security Operations Platform, as well as with other security tools, including SIEM, SOAR, and vulnerability management systems that may be part of an organization’s legacy security stack. This interoperability enables automatic updates and contextual data sharing, making it easier for security teams to apply threat intelligence directly to their threat models and ensure they are constantly updated with the latest insights.
6. Collaboration and Information Sharing
ThreatStream enables organizations to share threat intelligence internally and externally with trusted peers via information sharing and analysis centers (ISACs), enhancing situational awareness. This feature supports collaborative threat modeling by enabling teams to pool insights, broaden their understanding of threat landscapes that may affect their environments, and notify their industry peers of potential threats. For example, banks that compete fiercely for business will eagerly close ranks and work together when facing a common threat.
These features make ThreatStream a valuable ally in threat modeling, enabling organizations to build dynamic, data-driven models that evolve with the threat landscape and provide actionable insights for a more secure infrastructure.
The Power of Threat Modeling
Threat modeling is a strategic approach to proactively understanding, mitigating, and managing cybersecurity risks. By following structured steps — from defining objectives to validating results — organizations can build stronger defenses against sophisticated cyberattacks.
Leveraging threat intelligence platforms like Anomali ThreatStream enhances and accelerates each step by providing up-to-date data on threats, ensuring that security measures are both relevant, proactive, and effective. Through continuous improvement and adherence to best practices, threat modeling can be a powerful tool for managing cybersecurity risks.





