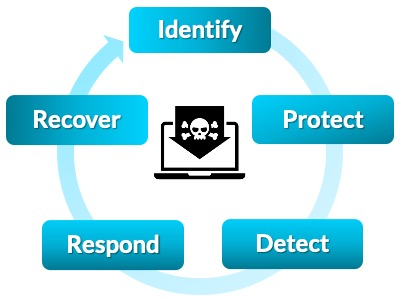
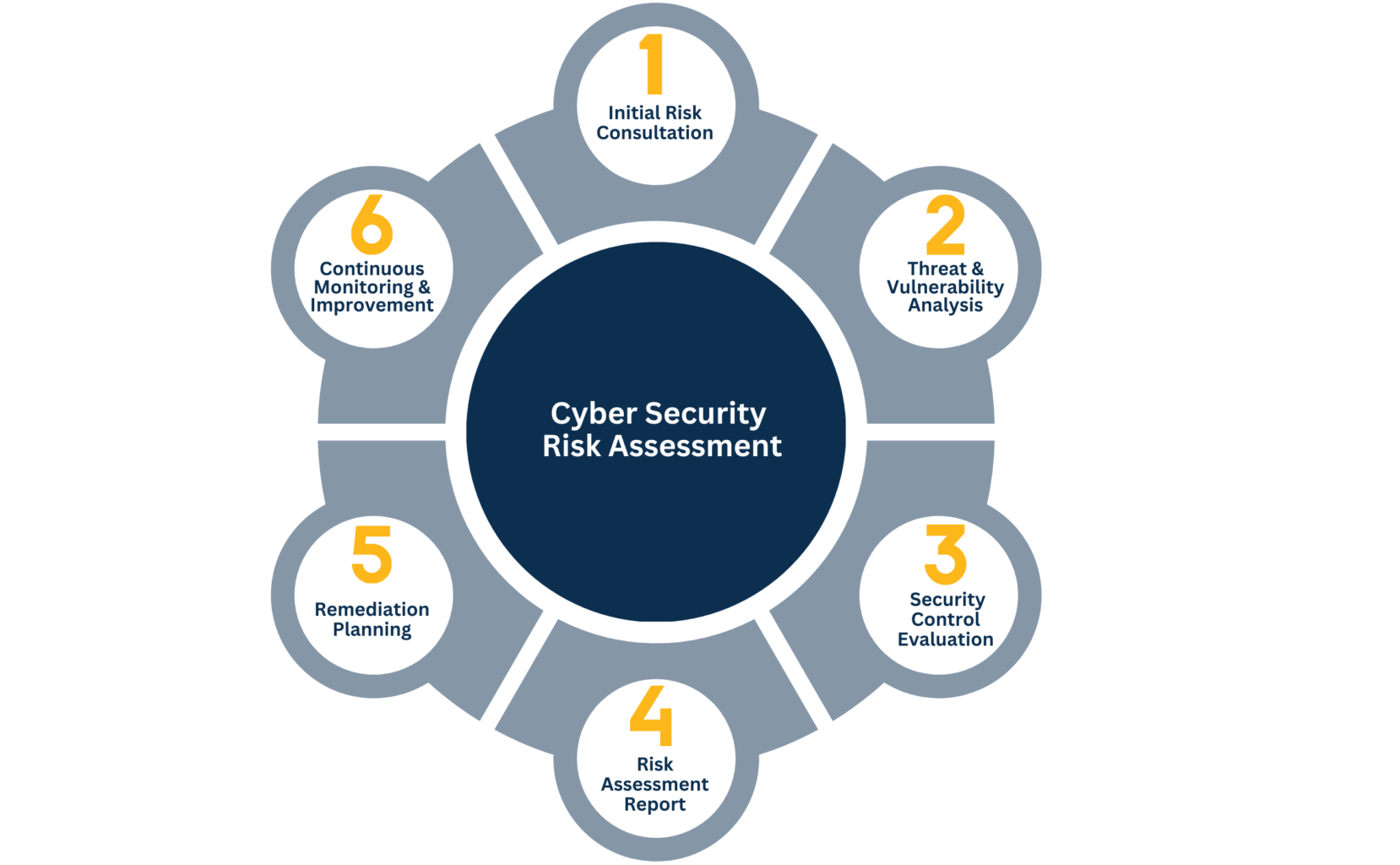
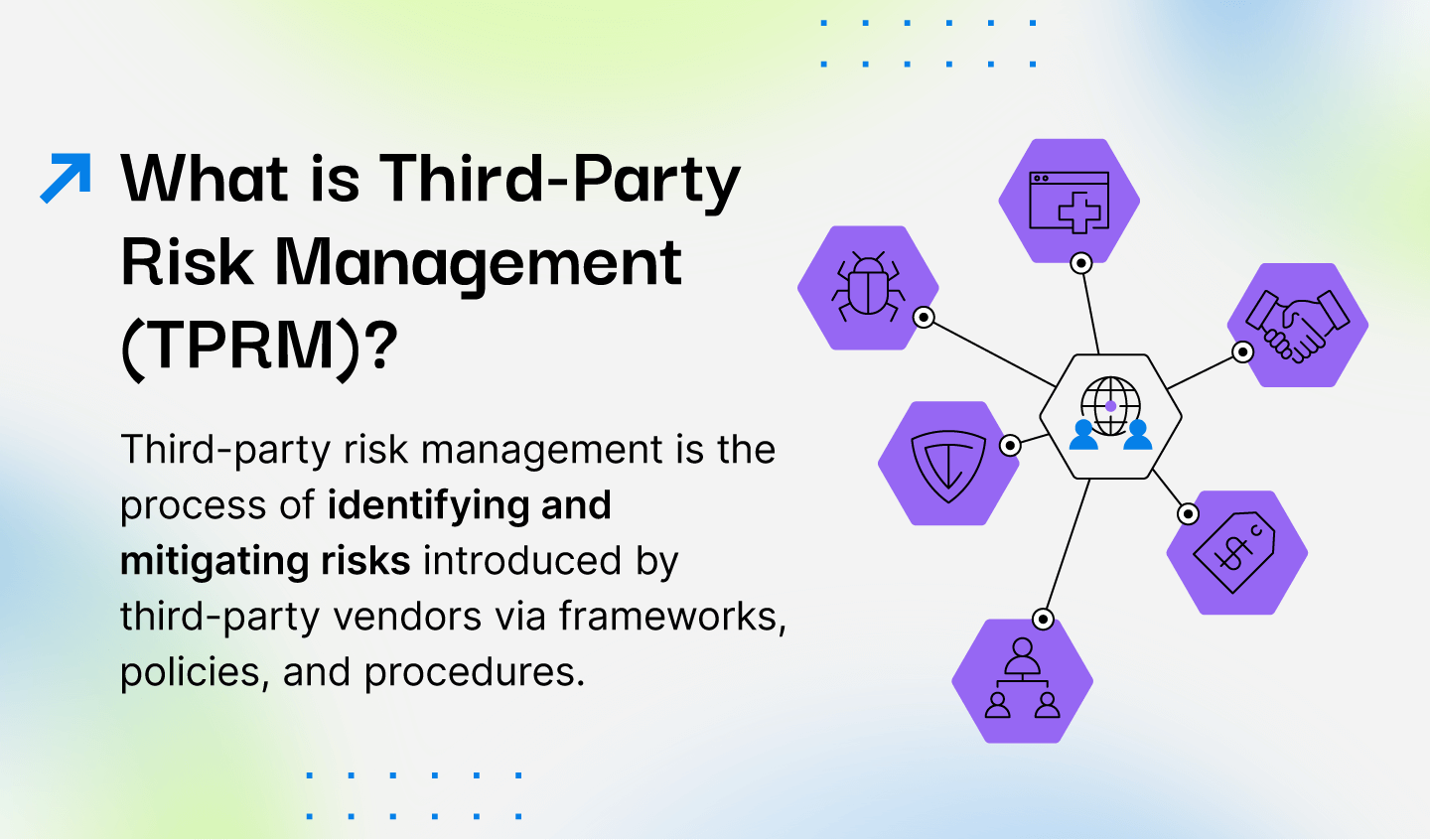
In today’s digital era, cyber threats, especially ransomware attacks, pose significant risks to organizations. Black Kite offers a comprehensive risk assessment service powered by OSINT techniques and industry-standard scoring models. It swiftly identifies vulnerabilities such as open ports, code execution flaws, and leaked credentials, providing understandable reports within hours. These reports help organizations assess their own and their suppliers’ susceptibility to Ransomware attacks.